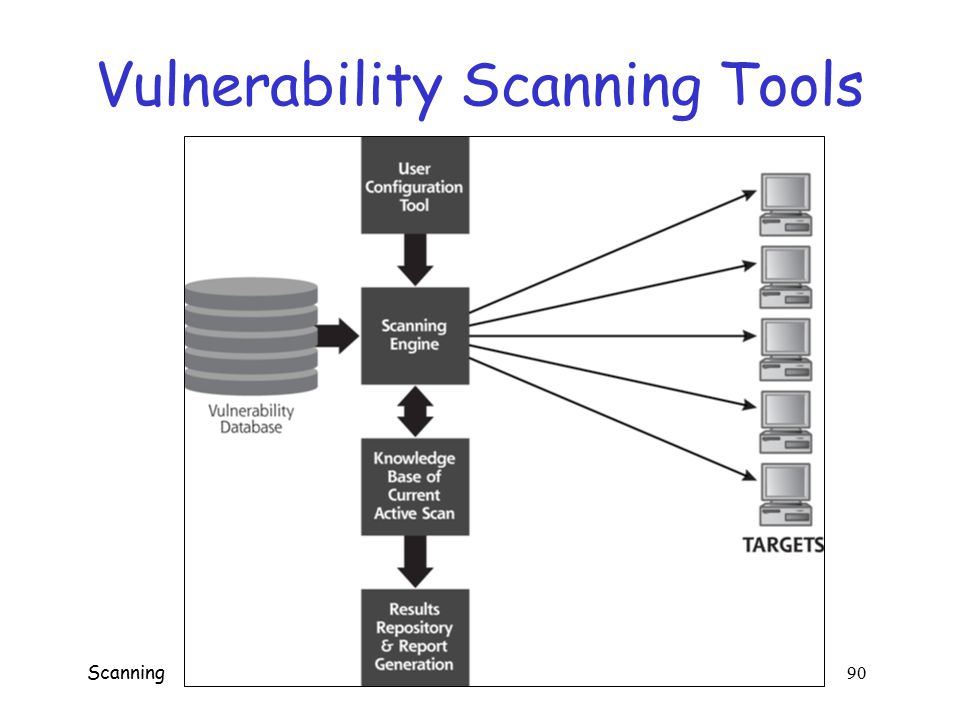
The history of digital world is blotched with several cyber attacks that have adversely effected numerous organizations and people. Present day hackers are much more active and progress in step with the cyber protection teams working tirelessly for securing the digital network. Cyber attackers find different ways to intrude a network and end up in compromising the network security. One such way in which the network security becomes vulnerable and can be compromised is via web application programs. Therefore it gets necessary to test every web application before deploying it in order to ensure that you network is safeguarded from every potential data breach. This is where the vulnerability scanning tools come into scenario.
A web application vulnerability scanner is a software program that automatically performs a black box testing on all the web applications and reports in case any vulnerability threat is found. However, they do not access the source code and only executes functional testing. Here we have provided a list of 6 such web application vulnerability scanning tools which you can deploy in your organization as per your requirement.
List of Various Web Application Vulnerability Scanners
The scanners listed in this section are in a random order and have not been listed as per their ranking. Have a look at various open-source web application security scanners which you can make use of:
1. Vega: Vega is one such vulnerability scannertool, which performs the security testing of all the web applications. It has been written in Java language and has a Graphic User Interface. The software supports various platforms like Linux, OS X, as well as Windows. It can search for vulnerabilities like directory listing, SQL injection, shell injection, header injection, file inclusion and much more. In case you want to extend this tool, it can be done with the help of a powerful Application Programming Interface written in JavaScript.
2. Grabber: Grabber is yet another web application vulnerability scanner which can scan the entire web applications. It can detect vulnerabilities like Ajax testing, cross site scripting, SQL injection, Backup file check, File Inclusion and JS Source code analyzer. This scanner should be mostly used with small web applications because they consume a lot of time in doing the scanning. Hence, it is mostly recommended for home users.
3. Wapiti: This is also one of the best vulnerability scanning tools, which enables the users to check the security of the desired web applications. It tests the web pages by scanning them and injecting data in them. It has the capability of detecting multiple vulnerabilities and supports both POSTHTTP and GET. This scanner can detect threats like file inclusion, file disclosure, command execution detection, CRLF injection, Cross Site Scripting, Backup files disclosure, and many others. Since it is a command-line application, the beginners may find it a little difficult to work with it.
4. Zed Attack Proxy: Also Known as ZAP, Zed Attack Proxy is available for Mac, Linux and Windows OS. It can be used to detect a vast range of vulnerabilities and is very easy to use. This can be of great importance for the beginners who are learning penetration testing. Its key functionalities include automatic scanner, intercepting proxy, fuzzer, traditional but powerful spiders, REST based API, Web Socket Support and much more. You can scan the web application be inserting the URLs in it.
5. Skipfish: This web application vulnerability scanner crawls the targeted website and then checks all the pages for any security threat and prepares a final report at the end of the analysis. Written in C language, this tool is highly optimized for HTTP handling and minimizes CPU utilization. The tool claims to offer supreme quality and very less false positives.
WebScarab: This web application scanner is based on Java framework and deploys HTTPS and HTTP protocols for analyzing the web applications. The functionality of the tool can be extended by the available plug-ins. Modifications can also be done before they have been received by the browser or the server. This tool serves best for all those who have apt knowledge of HTTP and is not suitable for the beginners.
So these are some of the vulnerability scanning tools which you can use for scanning the web applications for vulnerability scanning. Choose any of the above and get to work.